Purpose:
- Milligan operates perimeter firewalls between the internet and the university to provide a secure computing environment. This firewall policy governs how university firewalls will filter internet
traffic to mitigate risk.
Policy for Perimeter Firewalls:
The perimeter firewall permits the following for outbound and inbound internet traffic:
- Outbound – Allow internet traffic to hosts and services outside of the university. Some protocols may be restricted in order to protect the interests of the institution.
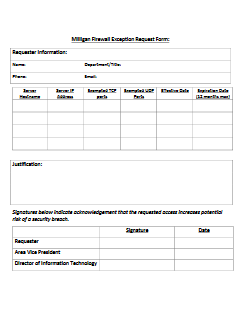
- Inbound – Allow internet traffic from outside the university that supports the mission of the university after approval of a firewall exemption request. All exemptions must be signed by the appropriate area vice president before submission to IT.
Information Technology will evaluate the risk of opening the firewall to accommodate requests. Where the risk is acceptable, granting of requests will be dependent on network infrastructure limitations and the availability of required resources to implement the request. If the risk associated with a given request is deemed objectionable, then an explanation of the associated risks will be provided to the original requestor and alternative solutions will be explored.
Operational Procedures:
Only firewall system administrators are permitted to logon to the firewall.
- Access to firewall hosts must be tightly controlled. Only firewall system administrators are allowed to have user accounts on firewall hosts.
- Firewall system administrators must have personal accounts; i.e. no group logins are allowed.
- Direct remote root access is not allowed. All root access must be via a personalized logon. Only personnel with the appropriate authorization can make changes to the firewall access rules, software, hardware or configuration.
- All changes should be as a result of a request recorded using the Firewall Change Request Form although emergency modifications can be requested by phone, with a follow up email and change request.
- Only authorized personnel must be able to implement the changes and an audit log
must be retained.
Logging and Compliance:
There must be an active auditing/logging regime to permit analysis of firewall activity either during or after a security event. An audit trail is vital in determining if there are attempts to circumvent the firewall security. Audit trails must be protected against loss or unauthorized modification. The firewall system must be able to provide logging of specific (or all) traffic when suspicious activity is detected.
Firewall Change Request Form: