Approved by President’s Cabinet Fall 2017, last modified Fall 2022
Purpose:
- The Department of Information Technology is responsible for acquiring and maintaining all software and hardware products, contracts, and services purchased with university funds. IT replaces hardware through a replacement cycle and maintains a software library that meets the needs of most users.
- IT will neither install nor support hardware or software that has not been approved in advance of purchase. IT can help with determining if Milligan already owns hardware and software to meet your needs.
Hardware:
Computer hardware includes desktop computers, laptops, tablets, printers, cameras, etc. Each full-time employee will be provided with the following baseline hardware configuration: one workstation or laptop, one monitor, one keyboard, one mouse, and one webcam upon request.
Large-capacity multi-functional devices that scan, copy, and print are available to all users. Employees should use these devices instead of purchasing small desktop printers.
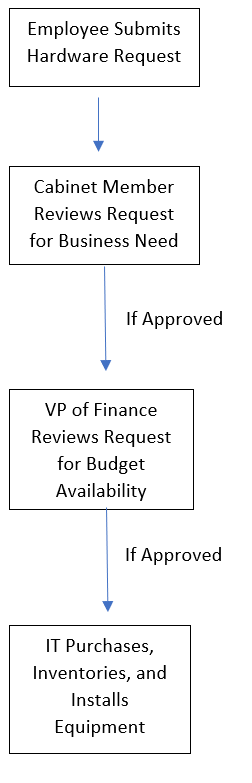
If an employee has a business need for hardware other than the baseline configuration, this may be requested by using the Specialty Hardware Request form. This form will be sent to the employee’s Cabinet member for approval. If the Cabinet member approves, she/he will send the request on to the VP of Finance to determine whether the purchase can be funded. Upon this approval, the request will be forwarded to the IT department for purchase, inventory, and installation.
Software:
IT provides a standard computer software image for new computers. This image creates a consistent technology environment that is secure and compliant with licensing agreements. Some departments may require additional software for work-related functions. If so, the following process applies:
- IT must be included in all software acquisitions, including cloud acquisitions, to ensure compliance with the campus infrastructure.
- All software vendor software demonstrations should include IT.
- IT will ensure that the software meets all operational requirements as well as the user needs. Additionally, the data hosting and storages services will be reviewed by IT.
- IT will assess the level of internal support necessary and those services will either be provided by IT or will need to be purchased from the vendor.
- All software quotes should be submitted by IT to the vendor so that the IT department can ensure the quotes are based on current system configurations, all discounts are included in the quote, appropriate licensing and support services are included, and educational and non-profit discounts are applied.
- Milligan IT will not install software that is unrelated to work. This includes, but is not limited to, screen savers, music or file sharing software, drivers/software for non-essential peripherals, etc. Milligan cannot ensure the proper functioning of these packages with other supported software, or that they will not cause future problems on the user’s system.
- IT will maintain an administrator account and root password for the system in a secure password management system. This enables IT to provide access to your system should changes in personnel occur unexpectedly.
- Software requests must be made through the Specialty Software Request Form.
Vendor Compliance:
All vendors that provide cloud-based services or on-premise software must meet acceptable industry security standards. The determination for compliance is based on several factors.
- Vendors must provide a HECVAT for risk assessment by IT.
- The software under review must provide a high-quality service that improves our technology environment without jeopardizing network or server performance, data integrity or data security.
- All software that requires data exchange that may include FERPA or HIPAA protected information must comply with all state and federal requirements.
- The contract data security rider must be utilized.
Hardware Approval Flow Diagram